Multizone | All our technotes
If we've published it, you can find it here.

Microsoft's recent announcement regarding the sunset of Windows Subsystem for Android (WSA) means the end of Amazon Appstore on Windows 11. This ripple is being felt throughout the tech press, sparking discussions about the company's technology shifts and the implications for users and developers alike. Here's an extract of Amazon's email
Discontinuation of Amazon Appstore on Windows 11
Starting March 6, 2024, Amazon Appstore will no longer be available for download from the Microsoft Store on Windows 11 devices. After March 5, 2025, Amazon Appstore on Windows 11 and any apps downloaded from it will not be supported.
In this article, we examine some of the murk surrounding this decision, examining its possible background, reasons, impact, industry response, and future implications. Here is Microsofts announcement:
TL:DR: Microsoft has thrown in the towel. Use a Chromebook or an Android tablet if you want seamless Android. Use an Emulator from Android Studio if you want recently updated emulators of Android devices.
- Details
Read more: Amazon Appstore and WSA heads off into the sunset
File Sharing securely with external users and with adequate governance is hard. You might think you can just easily mandate a file sharing Software as a Service (SaaS) platform as part of your productivity suite, (Google Workspace has Google Drive, Microsoft 365 has Microsoft OneDrive, Apple has iCloud or there's always a third party SaaS like the venerable DropBox), but hold on before you do so. In exchange for a simple user experience you give up control over your data hosting to the cloud service provider. That might be fine for your organisation, and it is for a lot of organisations, but for some data workloads with sensitive, private or privileged data it could well not be acceptable.
{ToC}
Five reasons why a Software as a Service (SaaS) platform might fail your organisations criteria for secure file sharing technology
There are probably more but here are five:
- Firstly, SaaS providers might be required to give access to their data to other agencies by regulation or for other reasons although like DropBox they may appear to be transparent about it.
- Secondly, they might index your content as Windows does if you let it by enabling "Cloud content search", leading to the potential for serving information in search results to users who should not be able to see it.
- Thirdly, your SaaS provider might harvest the data for use in training a large language model (LLM) for Artificial Intelligence (AI), with the resulting risk posited by Google in "Privacy Considerations in Large Language Models" that training data appears in output or could be subject to a training data extraction attack.
- Fourthly, they might change their terms and conditions or like Skiff be acquired and shut down.
- In extreme cases, (looking at you, Amazon Drive), they may just throw in the towel and cease operating the service altogether.
Evaluating secure file sharing against an information security policy framework
Recently, we conducted an evaluation of secure file sharing technology for suitability for sharing securely with users both internal and external to an organisation in a regulated market sector. This was an interesting exercise, which made us spend further time thinking about the issues around secure sharing of company information in the cloud, and the almost automatic use these days of the technologies tied to an organisations business cloud software provider. The criteria we set were informed by our own information security policy framework as we look to become ISO27001 certified.
Information Security Criteria
Whatever system is chosen must preserve information security. It should ensure that access to the system is only given to the right people, to the right data, and at the right time.
- Access Control – Measures to control who can access the data and what actions they can perform.
- Authentication – Authentication, authorisation and revocation mechanisms strong enough to verify the identity of users accessing the service.
- Auditing and Logging – Detailed logs of all activities and accesses to the data, allowing for accountability and traceability.
- Incident Response – Procedures to respond and mitigate changes, continuity, disaster, security incidents or breaches.
- Data Encryption – Encryption to protect data from unauthorized access.
- Data Integrity – Maintenance and assurance of data over its entire life-cycle.
- Data Deletion and Disposal – Supports procedures for securely deleting and disposing of data when it is no longer needed.
- Data Governance – Policies and procedures for the proper management and use of data within the organization.
- Data Classification – Data classification based on its sensitivity.
- Network Security – Prevention of unauthorized access and protection against external threats.
- Vendor Risk Management – Assessment and management of security risks associated with third-party vendors or partners involved in the data sharing process.
- User Training and Awareness – Education available to users about security best practices to help prevent security incidents.
- Secure Development Lifecycle – Security in the software development process must be respected.
- Security Monitoring – Tools and processes for continuous monitoring of the service and its environment for potential security issues.
- Compliance and Regulatory Requirements – Ensure that the service complies with relevant laws, regulations, and industry standards.
Functionality and ease of use
Functionality and ease of use only matters if the information security criteria are met.
- Ease of use – There should be a fully featured web App, Windows, Mac desktop drive/volume level support is desirable, folder level support acceptable. iOS and Android Apps are highly desirable.
- Functionality – Branded Portal, Let's Encrypt SSL support, Custom URL, Shared Files and Folders, (password protection, public, time timited), Unlimited storage. Comprehensive email notifications.
No system guarantees everything in an information security policy
This exercise is not about criticising systems that cannot guarantee total compliance with information security policies. None are perfect, It is more to show that if information security cannot be guaranteed then the risks should be quantified, written down, subject to regular review and accepted by the executive management of the business.
TL:DR: Operating system vendor solutions and well known SaaS services cannot easily be made to satisfy all of these conditions. The only way to guarantee compliance with strict information security policies is to self host with a technology and platform that enables you to encrypt your data in transit and at rest. You have to have the keys to the kingdom!
- Details
Read more: Secure file sharing information security policy framework
An Overview
Artificial Intelligence (AI) is a buzzword that seems to pop up everywhere these days. From virtual assistants like Siri and Alexa to self-driving cars and recommendation algorithms on streaming platforms, AI is making significant strides in transforming how we live and work. But what exactly is AI? What are its various forms? How is it shaping our future? In this article, we will delve into the world of AI, its subfields, benefits, limitations, and the ethical concerns surrounding this rapidly developing technology.
AI refers to the capability of machines to perform tasks that traditionally require human intelligence. This includes activities like speech and image recognition, decision-making, and language translation. One of the primary goals of AI research is to develop systems that can learn from experience, adapt to new inputs, and perform tasks quickly and accurately.
TL:DR – AI is upon us. This is a primer.
- Details
What is S3 Browser?
S3 Browser is a Freeware Windows client for Amazon Simple Storage Service (Amazon S3) A part of Amazon Web Services (AWS) Amazon S3 is a well regarded, highly available, resilient object storage service offering industry-leading scalability, data availability, security, and performance. If there is a criticism it is that it can be hard to navigate and hard to ensure security is implemented thoroughly. S3 Browser can help shine some light on your S3 Buckets and files, and its dead easy to use and powerful.
Main features
- Access Key ID based login
- Upload / Download with built in data integrity
- Publish
- Browse, create and delete S3 buckets
- Share S3 buckets
- Use other shared buckets
- Set Access Controls on S3 Buckets and files
- Create encrypted backups
- Manage Amazon CloudFront
TL:DR: If you use Windows, then this is an invaluable tool for working with Amazon S3 files and buckets from multiple Amazon S3 accounts. You should download it, upgrade to Pro and expense the modest cost! If you don't use Windows this is not for you.
- Details
Read more: S3 Browser, a little swiss army knife for AWS S3 buckets

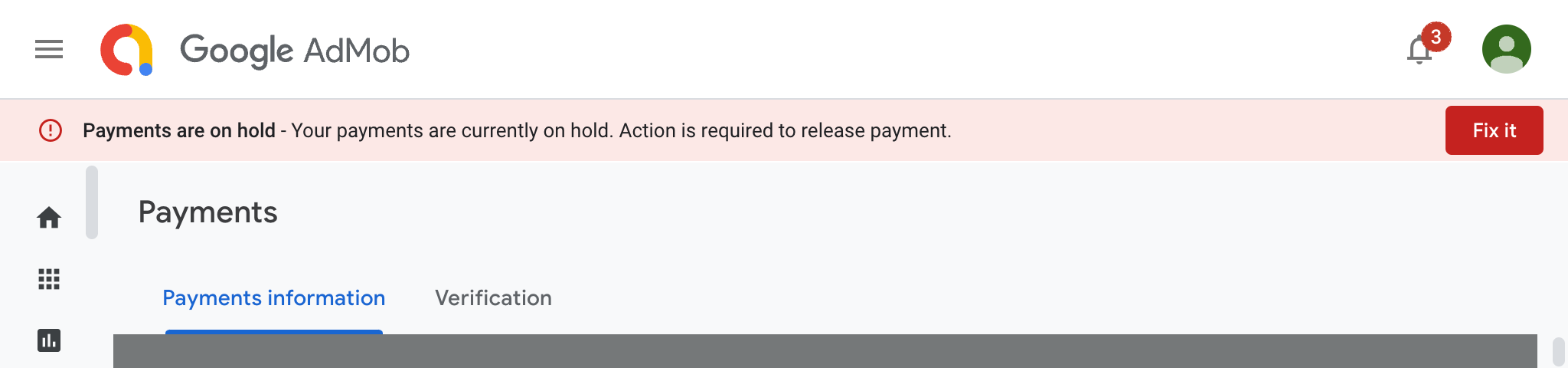
My Google payments for Apps using AdMob were on hold. Thats not good! How do you fix it?
- Details
Read more: Google payments on hold. Action is required - Taiwan

This document is an example security policy for the security of Apple Mac computers running macOS 14 Sonoma in a small business setting.
| Version | Significant changes |
|---|---|
| 1.3 | Updated for macOS 14 Sonoma |
| 1.3.1 | Version for LinkedIn |
| 1.3.2 | Updated with clarifications about supported versions of macOS |

TL:DR – I was asked if I had a security policy document for macOS that would work for a small business who don't have a device management platform and I did have one, but it was mostly in my head or implemented on my Macs, so I decided to write it up in detail.
It is an example. You might want to change things. It is for smaller businesses who can't use Apple Business Manager or similar device management technologies.
I thought it might be helpful to someone to post it here.
- Details
Read more: Hardening Macs - Security policy for macOS Sonoma

iOS 17
iOS 17 brought big updates to Phone, Messages and FaceTime that gave you new ways to express yourself as you communicate. StandBy delivers a new full-screen experience with glanceable information designed to be viewed from a distance when you turn iPhone on its side while charging. AirDrop makes it easier to share and connect with those around you and adds NameDrop for contact sharing. Enhancements to the keyboard make entering text faster and easier than ever before. iOS 17 also includes updates to Widgets, Safari, Music, AirPlay and more.
TL:DR— Install right away if your device is eligible just to get the updates and Security fixes. Consider selling/trading in iPhones older than the iPhone XS as they won't be upgradable to iOS 17 and their value is diminishing. iOS 17 compatible iPhone devices with a lightniing connector are also on borrowed time, but do not need to be immediately replaced. App developers might find it helpful to keep an iPhone 8 or iPhone X around for testing with iOS 16 while it is still supported.
- Details
- Distribute insights in an Power BI app
- Using developer tools to transfer files on Android
- Quick and easy 𝕏 Logo for Twitter for documents and websites
- How to download tweets & delete your twitter account
- Pixelbook chromebook choices for developers
- Kali Linux on Windows 11
- Amazon Fire Max 11 - best value for the money tablet
- Worried about metadata leakage - mdls can help
- Getting started with Power Platform PowerApps CLI
- Use an Apple Magic Mouse on Windows 11 PC
- Use GitHub to deploy your Power Platform app (part 4)
- Publish Power Apps securely via GitHub (part 3)
